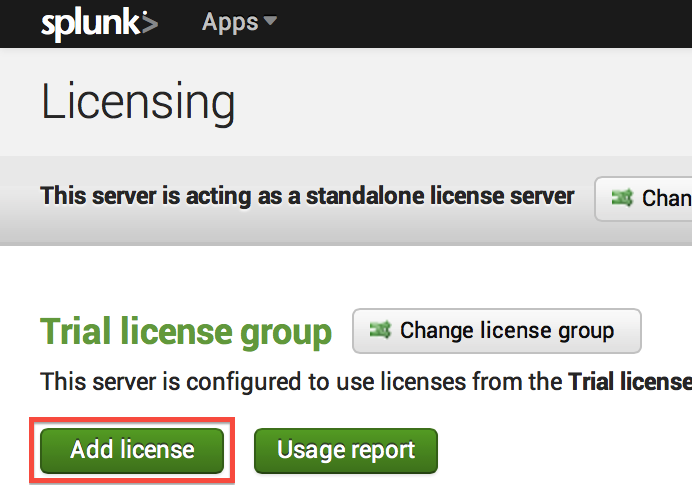
- Search capabilities return when you have fewer than 5 (Enterprise) or 3 (Free) violations in the previous 30 days or when you apply a new license with a larger volume limit. Note: During a license violation period, Splunk does not stop indexing your data. Splunk only blocks access while you exceed your license.
- The enterprise license starts at $6,000 for a 500MB/day perpetual license or $2,000/year for a term license; Its a tiered license. Bigger the license cheaper it i s; Once you license Splunk Enterprise there is no limit to the number of users, searches, alerts, correlations, reports, dashboards or automated remedial actions.
Stingray boat service manual. Check out for more details $7000 USD worth of material for just $149. Check out the Complete Course on Udemy (COUPON: YOUTUBE) https://w. Skyrim bloodskal sword.
The fields and tags in the Certificates data model describe key and certificate management events from a variety of secure servers and IAM systems.

Splunk License Keygen Download
Note: A dataset is a component of a data model. In versions of the Splunk platform prior to version 6.5.0, these were referred to as data model objects.
Tags used with Certificates event datasets
The following tags act as constraints to identify your events as being relevant to this data model. For more information, see How to use these reference tables.

| Dataset name | Tag name |
|---|---|
| All_Certificates | certificate |
| ssl OR tls |
Fields for Certificates event datasets
The following table lists the extracted and calculated fields for the event datasets in the model. The table does not include any inherited fields. For more information, see How to use these reference tables.
The key for using the column titled 'Abbreviated list of example values' follows:
- Recommended: Add-on developers make a best effort to map these event fields. If these fields are not populated, then the event is not very useful.
- Required: Add-on developers map these event fields when using the pytest-splunk-addon to test for CIM compatibility. See pytest-splunk-addon documentation.
- Prescribed fields: Permitted values that can populate the fields, which Splunk is using for a particular purpose. Other valid values exist, but Splunk is not relying on them.
- Other values: Other example values that you might see.
| ||||
| SSL | ssl_issuer_common_name | string | The certificate issuer's common name. |
|
| SSL | ssl_issuer_email | string | The certificate issuer's email address. | |
| SSL | ssl_issuer_email_domain | string | The domain name contained within the certificate issuer's email address. | recommended |
| SSL | ssl_issuer_locality | string | The certificate issuer's locality. | |
| SSL | ssl_issuer_organization | string | The certificate issuer's organization. | |
| SSL | ssl_issuer_state | string | The certificate issuer's state of residence. | |
| SSL | ssl_issuer_street | string | The certificate issuer's street address. | |
| SSL | ssl_issuer_unit | string | The certificate issuer's organizational unit. | |
| SSL | ssl_name | string | The name of the ssl certificate. | |
| SSL | ssl_policies | string | The Object Identification Numbers's of the certificate's policies in a comma separated string. | |
| SSL | ssl_publickey | string | The certificate's public key. | |
| SSL | ssl_publickey_algorithm | string | The algorithm used to create the public key. | |
| SSL | ssl_serial | string | The certificate's serial number. |
|
| SSL | ssl_session_id | string | The session identifier for this certificate. | |
| SSL | ssl_signature_algorithm | string | The algorithm used by the Certificate Authority to sign the certificate. | |
| SSL | ssl_start_time | time | This is the start date and time for this certificate's validity. Needs to be converted to UNIX time for calculations in dashboards. | recommended |
| SSL | ssl_subject | string | The certificate owner's RFC2253 Distinguished Name. |
|
| SSL | ssl_subject_common_name | string | This certificate owner's common name. |
|
| SSL | ssl_subject_email | string | The certificate owner's e-mail address. | |
| SSL | ssl_subject_email_domain | string | The domain name contained within the certificate subject's email address. | recommended |
| SSL | ssl_subject_locality | string | The certificate owner's locality. | |
| SSL | ssl_subject_organization | string | The certificate owner's organization. | required for pytest-splunk-addon |
| SSL | ssl_subject_state | string | The certificate owner's state of residence. | |
| SSL | ssl_subject_street | string | The certificate owner's street address. | |
| SSL | ssl_subject_unit | string | The certificate owner's organizational unit. | |
| SSL | ssl_validity_window | number | The length of time (in seconds) for which this certificate is valid. | required for pytest-splunk-addon |
| SSL | ssl_version | string | The ssl version of this certificate. |
Examples for Certificates event datasets
The following is a sample of a certificate event from zeek/corelight:
Splunk Enterprise License Keygen
The following are CIM fields extracted from this sample:
You can monitor license usage with the Deployment Monitor App. The license usage page shows a wide range of historical information. There's also a license report page page that provides details on daily license usage over a 60 day period.
License usage page
The license usage page in the deployment monitor contains two charts: one that shows the cumulative MB of data per day by source type, and a histogram that shows MB of data received across selectable criteria, including source type, host, source, indexer, forwarder, and license pool.
Further down the page, there's detailed information on usage statistics, with separate listings for several criteria, including sourcetype, host, source, indexer, forwarder, and license pool.
License report page

Splunk License Keygen Download
Note: A dataset is a component of a data model. In versions of the Splunk platform prior to version 6.5.0, these were referred to as data model objects.
Tags used with Certificates event datasets
The following tags act as constraints to identify your events as being relevant to this data model. For more information, see How to use these reference tables.
| Dataset name | Tag name |
|---|---|
| All_Certificates | certificate |
| ssl OR tls |
Fields for Certificates event datasets
The following table lists the extracted and calculated fields for the event datasets in the model. The table does not include any inherited fields. For more information, see How to use these reference tables.
The key for using the column titled 'Abbreviated list of example values' follows:
- Recommended: Add-on developers make a best effort to map these event fields. If these fields are not populated, then the event is not very useful.
- Required: Add-on developers map these event fields when using the pytest-splunk-addon to test for CIM compatibility. See pytest-splunk-addon documentation.
- Prescribed fields: Permitted values that can populate the fields, which Splunk is using for a particular purpose. Other valid values exist, but Splunk is not relying on them.
- Other values: Other example values that you might see.
| ||||
| SSL | ssl_issuer_common_name | string | The certificate issuer's common name. |
|
| SSL | ssl_issuer_email | string | The certificate issuer's email address. | |
| SSL | ssl_issuer_email_domain | string | The domain name contained within the certificate issuer's email address. | recommended |
| SSL | ssl_issuer_locality | string | The certificate issuer's locality. | |
| SSL | ssl_issuer_organization | string | The certificate issuer's organization. | |
| SSL | ssl_issuer_state | string | The certificate issuer's state of residence. | |
| SSL | ssl_issuer_street | string | The certificate issuer's street address. | |
| SSL | ssl_issuer_unit | string | The certificate issuer's organizational unit. | |
| SSL | ssl_name | string | The name of the ssl certificate. | |
| SSL | ssl_policies | string | The Object Identification Numbers's of the certificate's policies in a comma separated string. | |
| SSL | ssl_publickey | string | The certificate's public key. | |
| SSL | ssl_publickey_algorithm | string | The algorithm used to create the public key. | |
| SSL | ssl_serial | string | The certificate's serial number. |
|
| SSL | ssl_session_id | string | The session identifier for this certificate. | |
| SSL | ssl_signature_algorithm | string | The algorithm used by the Certificate Authority to sign the certificate. | |
| SSL | ssl_start_time | time | This is the start date and time for this certificate's validity. Needs to be converted to UNIX time for calculations in dashboards. | recommended |
| SSL | ssl_subject | string | The certificate owner's RFC2253 Distinguished Name. |
|
| SSL | ssl_subject_common_name | string | This certificate owner's common name. |
|
| SSL | ssl_subject_email | string | The certificate owner's e-mail address. | |
| SSL | ssl_subject_email_domain | string | The domain name contained within the certificate subject's email address. | recommended |
| SSL | ssl_subject_locality | string | The certificate owner's locality. | |
| SSL | ssl_subject_organization | string | The certificate owner's organization. | required for pytest-splunk-addon |
| SSL | ssl_subject_state | string | The certificate owner's state of residence. | |
| SSL | ssl_subject_street | string | The certificate owner's street address. | |
| SSL | ssl_subject_unit | string | The certificate owner's organizational unit. | |
| SSL | ssl_validity_window | number | The length of time (in seconds) for which this certificate is valid. | required for pytest-splunk-addon |
| SSL | ssl_version | string | The ssl version of this certificate. |
Examples for Certificates event datasets
The following is a sample of a certificate event from zeek/corelight:
Splunk Enterprise License Keygen
The following are CIM fields extracted from this sample:
You can monitor license usage with the Deployment Monitor App. The license usage page shows a wide range of historical information. There's also a license report page page that provides details on daily license usage over a 60 day period.
License usage page
The license usage page in the deployment monitor contains two charts: one that shows the cumulative MB of data per day by source type, and a histogram that shows MB of data received across selectable criteria, including source type, host, source, indexer, forwarder, and license pool.
Further down the page, there's detailed information on usage statistics, with separate listings for several criteria, including sourcetype, host, source, indexer, forwarder, and license pool.
License report page
The license report page provides information on daily license usage. You can use this information to help estimate your license needs.
Splunk License Keygen Software
At the top of the page, there's a usage summary that provides peak and average usage statistics. Next, there's a chart that shows daily volume over the last four weeks. Finally, there's detailed information on daily usage over the last 60 days, ordered by indexer or license pool.
